How “Fansmitter” Malware Can Steal Data from Air-Gapped Computers
How “Fansmitter” Malware Can Steal Data from Air-Gapped Computers
Changing a computer’s fan speed produces an audio signal that can be hijacked to steal data, say computer security experts who have tested the technique.
When it comes to computer security, the ultimate protection is the “air gap”—a physical space between a computer and the Internet to ensure that the device is entirely isolated from the dangerous world of hacking.
But while air-gapping computers is an effective way to protect them, it is not perfect. In recent years, computer security experts have devised various fiendish strategies for extracting information from these devices. One is to commandeer the computer’s built-in speakers and use them to send data ultrasonically to a nearby recording device, such as a mobile phone. Indeed, some security researchers claim to have seen exactly this kind of ultrasonic malware in the wild.
The best countermeasure for this kind of attack is obvious: remove the speakers. Without speakers to generate sound, a computer cannot leak data acoustically. Or so everyone thought.
Today, Mordechai Guri and pals at Ben-Gurion University in Israel say they’ve found another way to hack air-gapped computers, this time by commandeering the computer’s fan and modifying its rotation rate to control the sound it produces. They call this new approach a “fansmitter.”
Fansmitters are simple in principle. Almost all computers use fans to cool the main CPU and the graphics card, and to pump air through the chassis. When they’re operating normally, the main sound produced by these fans is the result of rotating blades forcing air past static vanes.
The frequency of this sound depends on the number of blades and their rate of rotation. It is usually in the region of hundreds of hertz. Any alteration to this rotation rate changes the frequency of the sound.
This is the basis of their approach. These guys have created malware that alters the rotation speed, and hence sound, of a computer fan to encode data.
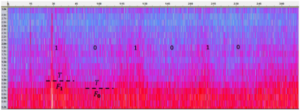
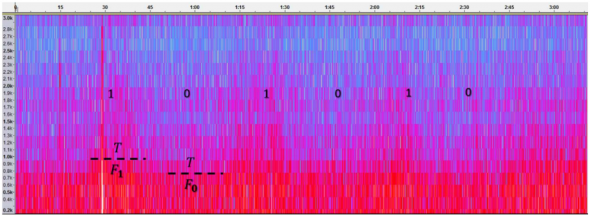
The malware transmits information using a special protocol in which the information is divided into packets made up of a preamble and a payload. The preamble consists of the signal 1010, which a listening device can use for calibration. This is followed by a payload of 12 bits that encode the data to be transmitted. This can be picked up by any listening device nearby, such as a smartphone.
One potential problem is that a user might notice, and become suspicious of, the variations in fan noise. So Guri and co use low frequencies of 140 to 170 hertz, which are more difficult for humans to hear. “Modulating the data over change of close frequencies is also less noticeable by a user, as it blends in and appears as natural background environmental noise,” they say.
Finally, the team put their malware through its paces by using it to control both a CPU fan and a chassis fan, both of which are common on today’s computers. As a receiver, they used a Samsung Galaxy S4 smartphone with a microphone sampling at 44.1 hertz. The testing environment was their computer lab with ordinary background noise, seven workstations, several network switches, and an active air-conditioning system.
The rate at which the team could send information was limited by the distance between the smartphone and the computer, and by the amount of background noise. Nevertheless, they were able to transmit at rates of up to 900 bits per hour. “Using our method we successfully transmitted data from air-gapped computer without audio hardware, to a smartphone receiver in the same room,” boast the team.
Guri and co say the technique can be applied to other devices too. “We show that our method can also be used to leak data from different types of IT equipment, embedded systems, and IoT devices that have no audio hardware, but contain fans of various types and sizes,” they say.
That’s interesting work that will give computer security experts yet another reason to worry. Countermeasures are many and relatively straightforward. The most obvious is to keep sensitive computers in restricted areas where mobile phones and other recording devices are banned. Another is to generate so much background noise that acoustic transmissions are impossible. Then there is the possibility of replacing any fans with specialized quiet ones or using water cooling instead.
But all these add yet another layer of precaution and complexity to an already overburdened computer security industry. The truth is that it is impossible to achieve perfect security. The only thing that can be guaranteed is that if you are worried about your computer leaking information, you will have plenty of sleepless nights ahead.
Ref: arxiv.org/abs/1606.05915 : Fansmitter: Acoustic Data Exfiltration from (Speakerless) Air-Gapped Computers

Leave a Reply