Quantum Cryptographers Set 400K Distance Record
Quantum Cryptographers Set 400K Distance Record
After falling victim to hackers, quantum cryptographers are fighting back with a more secure system capable of sending messages further than ever before.
Quantum cryptography is a method of transmitting information from one point in space to another so that it cannot leak out along the way. It is provably, perfectly secure, guaranteed by the laws of physics. In effect, it is the universe’s way of keeping secrets.
At least in theory. In practice, things have turned out to be more tricky. The problem is that while the laws of physics guarantee perfect secrecy, the equipment used to perform this type of cryptography is flawed. For example, lasers that are supposed to send single photons one at a time sometimes send several unexpectedly, and this allows supposedly secret information to leak out.
Hackers have already exploited these vulnerabilities to hack quantum cryptography systems, as this blog has reported. The worrying truth is that quantum cryptography has not proved to be as secure as theoretical physicists once promised.
But physicists have been fighting back. Soon after the first quantum hack in 2010, physicists devised a new quantum protocol for encrypting information that does not depend on a specific device to work. The trick is to use additional quantum states as decoys. So-called device-independent quantum cryptography suddenly made it possible to send information securely again.
Various teams have tried device-independent quantum cryptography and shown that it works. But there is a problem. It is slow—snail-blazingly, slothfully slow. The best demonstration so far sent information over a distance of 200 kilometers at a data rate of just 0.018 bits per second. At this rate, perfectly secure quantum cryptography would never be practical.
Today that changes thanks to the work of Hua-Lei Yin at the University of Science and Technology of China in Hefei, and a few pals who unveil a record-breaking demonstration of a form of device-independent quantum cryptography for the first time.
The security of quantum cryptography rests on the ability to send a one-time key that can then be used to send a classical message securely. So-called one-time pads are known to be perfectly secure, provided the key is used only once. So the problem boils down to finding a way to send this key using quantum methods; physicists call it quantum key distribution.
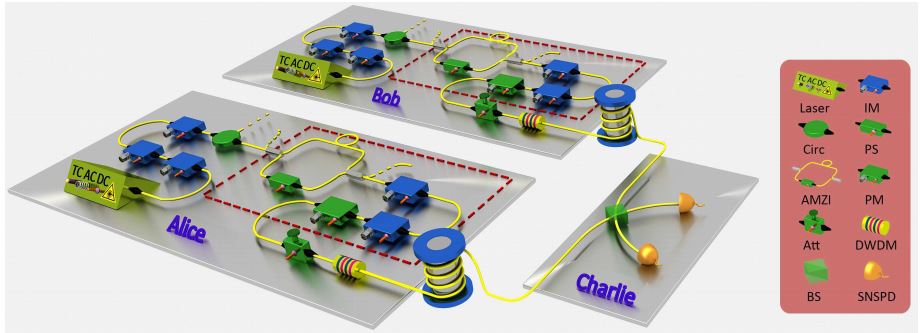
Hua-Lei and co have sent a key over a distance of more than 100 kilometeres at data rates measured in kilobits per second, and they have even managed distances of over 400 kilometers at lower data rates. “This is by far the longest distance reported for all kinds of quantum key distribution systems,” say the team.
And they’ve done this in a way that does not depend on the way the photons are detected. So there is no way a hacker can eavesdrop on the message by hacking into the photon detectors.
That’s an important advance that has the potential to restore faith in quantum cryptography, at least in part.
But there are some caveats. The first is that the method is only partially device independent. The trick these guys have perfected is a way to make the cryptography independent of the photon detectors. They call it measurement-independent quantum cryptography. However, it is still possible for the transmitter to be hacked.
Physicists argue, though, that transmitters can be tested in a safe laboratory before transmission, to ensure they are not compromised. So the feeling is that, for the moment at least, the best practical compromise is to pursue measurement-independent quantum cryptography.
But there is an even more serious concern. This is the fear that manufacturers of quantum transmitters or receivers could build in a quantum memory that stores information before it is transmitted and later reveal it to an eavesdropper during another transmission. Detecting this kind of Trojan hack would be more or less impossible without destroying the device.
The Chinese team’s setup cannot get around this. Indeed, the only way to counter a Trojan hack of this kind would be to make single-use quantum transmitters and receivers that are only used once. That’s an option so expensive and impractical that it may never be possible.
In the meantime, people who want to send secure messages will have to be satisfied with measurement-independent quantum cryptography, which promises (almost) perfectly secure messages, guaranteed by the laws of physics. And for many, that should be good enough.
Ref: arxiv.org/abs/1606.06821 : Measurement Device Independent Quantum Key Distribution Over 404 Km Optical Fibre

Leave a Reply